200 million social media records filtered in data violation x Major X
X, previously known as Twitter, has recently been in the headlines, with Elon Musk claiming that computer pirates have been trying to interrupt the platform. However, the most recent news that involves the social media site is particularly alarming and puts its users at serious risk.
Earlier this month, reports of significant data violation that involves X, after a self -proclaimed data enthusiastic known as “Thinkingone” said, claimed to have published a database that contains more than 200 million user records in a popular hacker forum. The leaked data include names, email addresses and almost everything else associated with the user’s profile X.
Stay protected and informed! Get security alerts and expert technology tips – Register in ‘The Cyberguy Report’ of Kurt now.

X application on an iPhone (Kurt “Cyberguy” Knutsson)
What you need to know
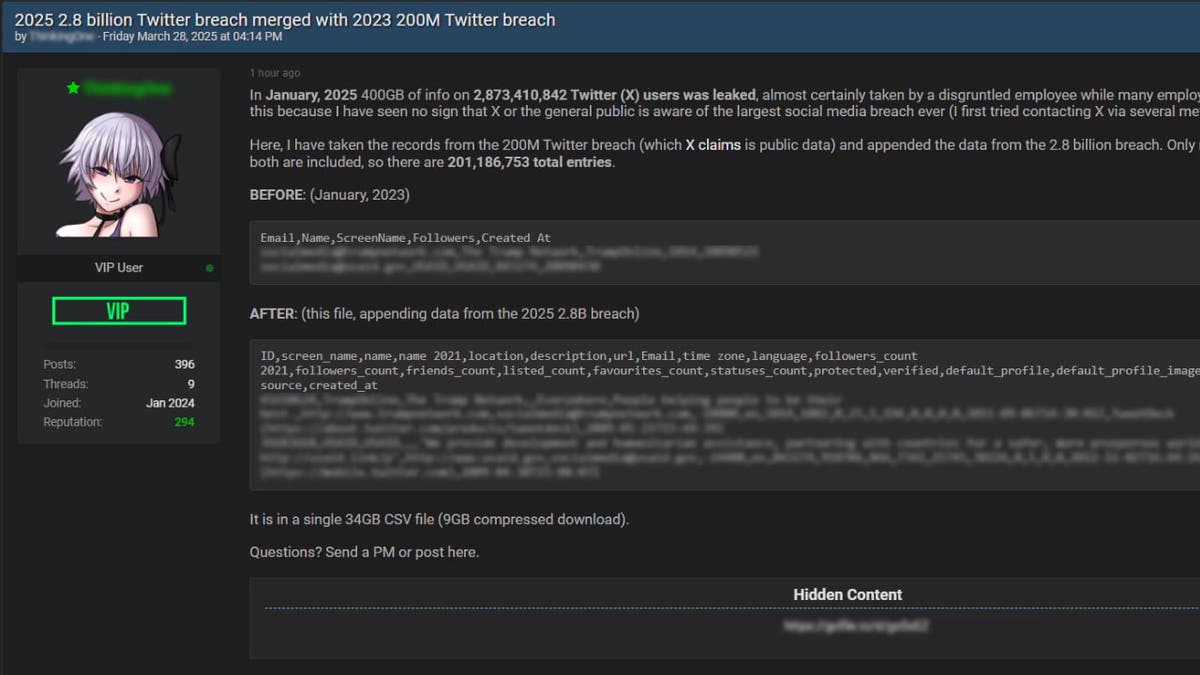
The X Data Leak is Believed To Stem from A Combination of Breaches, Including to Massive One That Allegedly Occurred in January 2025 and Another in 2023. The Leaked DataSet, reported 34 GB CSV File, Contains 201,186,753 Entries With Information Such As X Screen Names, User IDS, Full Names, Locations, Email Addresses (From The 2023 Breach), Follower Counts, Profile Data, Time Zones and Profile images.
Thinkingon said the data were referenced from a greater violation that involves 2.8 billion identifications and unique Twitter screen names. This violation may have been linked to internal work during layoffs in X, although the company has not verified this claim. Cybersecurity researchers, including those of Security detectivespartially confirmed the authenticity of the data by matching a sample with X Public X profiles and verify some email addresses. However, they could not completely confirm the property.
The violation seems to go back to a vulnerability identified in January 2022 through the Twitter error rewards program. This defect allowed attackers to access user data using only an email address or telephone number. Although the vulnerability was paved, the compromised data seem to have resurfaced in later leaks.
Partial confirmation of the data (security detectives) (Kurt “Cyberguy” Knutsson)
Malware exposes 3.9 billion passwords in a great threat of cybersecurity
Data violation puts X users at risk
The 2025 incident alone does not include passwords or financial information, but when combined with the email addresses of the 2023 filtration, the risk of phishing and social engineering attacks increases significantly. X has not officially recognized this specific violation at the time of writing, although it previously minimized the 2023 incident by stating that mainly involved public data.
The total of 2.8 billion records far exceeds 335 to 600 million active X users, suggesting that the data set may include inactive accounts, bots or historical data. While the complete scope and the impact of the violation are still clear, the incident highlights the continuous security challenges for the platform, especially after its acquisition by XAI at the end of March 2025.

X logo on a smartphone (Kurt “Cyberguy” Knutsson)
How to delete your private Internet data
7 ways in which it can be kept safe from the violation of data x
If you have an X or believe that your data may have been part of the violation, here there are seven important steps that you can take to protect.
1) Use strong antivirus software
This violation included email addresses linked to accounts X, main fuel for phishing attacks. Computer pirates can now send emails that seem to be of X, Musk or support, asking you to “verify your” or “restore your password.” These often contain attachments or files that can install malware or steal personal data.
The best way to safeguard the malicious links that install malware, which potentially access their private information, is to have strong antivirus software installed on all its devices. This protection can also alert it to the PHISHING Electronic Correos and Ransomware scams, maintaining their personal information and their safe digital assets. Get my elections for the best antivirus protection winners 2025 for your Windows, Mac, Android and iOS devices.
2) Eliminate your personal internet data
Since this Row X was exposed complete names, email addresses and other details of the public guidance profile, computer pirates can easily refer it with other data broker sites to create a full profile in you. This could lead to impersonation or pHishing of spear.
To reduce your exposure, use a reliable data disposal service that scan the data broker websites and request the elimination of your personal information. While no service promises to eliminate all its Internet data, having an elimination service is excellent if you want to monitor and automate the process of eliminating your information from hundreds of sites continuously for a longer period of time. See my best selections to obtain data removal services here.
3) Change the password of your x account
Although this particular violation may not have included passwords, there is still a significant risk, especially if you use the same password on several platforms. Once the attackers have their email, they often try to use it with common or previously filtered passwords to divide into accounts.
To change the password of your x account, go to Configuration and privacy From your profile menu, then select Your account and touch Change your password. Enter your current password, establish a new safe password and confirm the change. You can do this through the mobile application or starting session through the web. Consider using a password administrator to generate and store complex passwords. Get more details about me The best password administrators reviewed by experts of 2025 here.
4) Make your X profile more private to reduce future risk
Adjust the privacy settings of your X account to limit the visibility of personal information, such as making your profile private. Make sure only the necessary information is publicly visible. The information that seems harmless, such as its location, work or birthday, can be used by cybercriminals to impersonate you or guess your login credentials. If your profile X includes any personal detail that is not necessary, now is the time to eliminate them.
Maintaining its minimum profile not only protects your privacy, but also makes it more difficult for scammers to create convincing pHishing messages or social engineering attacks. Think twice before publishing updates or personal details, especially if they can be used to guess passwords or verify your identity.
Gonna Configuration> Privacy and Safety and block the visibility of your account.
5) Enable two factors (2FA) authentication for its X and email accounts
If the computer pirates received their email from the X violation, they can try to restore their password. 2fa It helps to stop this by requireing a second code to log in:
- Use an authenticator application like Google Authenticator or Authy, no SMS, which can be intercepted
- Secure your email accounts too, as they can be used to restore your credentials x
6) Use a Public Wi-Fi
Protect your data by accessing X or other platforms in public networks using a VPN to encrypt your connection. This will help to safeguard your information to be intercepted by malicious actors. A reliable VPN is essential to protect your online privacy and guarantee a safe high -speed connection. To get the best VPN software, see my expert review of the best VPN to navigate on the private web on its Windows, Mac, Android and iOS devices.
7) Register in the protection of identity theft to catch if your related information is abused
With more than 200 million names and email addresses exhibited, scammers can try to open accounts in your name or use your email in fraud attempts. Good identity protection can alert it if your information is sold on the dark website. You can also help you freeze your bank and credit card accounts to avoid greater unauthorized use by criminals. See my advice and the best selections on how to protect yourself from identity theft.
New Phishing Scam Outsmarts Security Codes to steal your information
Kurt key takeway
Violation X is another reminder that repairing vulnerability is just a piece of a much larger puzzle. The persistence of the leaked data, years after the original defect was revealed and set, highlights the long exposure tail that comes with large -scale violations. Even when credentials are not involved, the combination of identifiers such as email addresses, names and social connections can be armed through correlation attacks, data enrichment and social engineering assisted by AI-AI.
Do you feel that companies are doing enough to protect your data from computer pirates and other cyber threats? Get us knowing in Cyberguy.com/contact.
To obtain more technological tips and safety alerts, subscribe to my free Cyberguy Report newsletter when you head Cyberguy.com/newsletter.
Ask Kurt a question or let us know what stories we would like to cover.
Follow Kurt in his social channels:
- YouTube
Answers to the most informed Cyberguys questions:
- What is the best way to protect your MAC devices, Windows, iPhone and Android to be pirate?
- What is the best way to stay private, safe and anonymous while navigating the web?
- How can I get rid of robocalls with data elimination applications and services?
- How do I eliminate my private internet data?
New Kurt:
- Try the new Cyberguy games (crosswords, words searches, trivia and more!)
- Cyberguy exclusive coupons and offers
Copyright 2025 Cyberguy.com. All rights reserved.
Kurt “Cyberguy” Knutsson is a award -winning technological journalist who has a deep love for technology, equipment and devices that improve life with their contributions for News & News Business Startzing Mornings in “News & Friends”. Do you have a technological question? Get the free Kurt’s free newsletter, share your voice, an idea of the story or comment on Cyberguy.com.



