Clickfix malware deceives him to infect his own PC with Windows
Clickfix is a social engineering trick that computer pirates have been using more and more since early 2024 to spread malware.
It is deceiving you to execute malicious commands in your own computer, and the attack is now more common than ever. Computer pirates are causing people to install password theft malware causing a series of keyboard shortcuts, all under the claim to demonstrate that they are not bots.
Bots are automated computer programs that perform repetitive online tasks, often imitating human behavior. When deceiving him to prove that they are not bots, computer pirates exploit their lack of understanding about these automated systems so that malware is not installed.
Stay protected and informed! Get security alerts and expert technology advice: register in the Kurt Cyberguy report now

A person working on a laptop (Kurt “Cyberguy” Knutsson)
What you need to know
As reported by Krebsosecurythe last clickfix campaign deceives him to install password robbery malware with the appearance of a routine “verify that it is a human test.” Initially seen in specific attacks, it has now become conventional, which affects industries such as hospitality and medical care.
The scam begins when visiting a pirate or malicious website and you see a fake captcha style. By clicking on the “I am not a robot” button, it triggers a set of instructions asking you to press specific keyboard shortcuts. First, it is told to press Windows + R, which opens the Windows dialogue. It is then indicated that Ctrl + V is pressed, which walks a malicious script copied from the virtual clipboard of the website. If you press Enter, a script is executed that downloads and executes malware.
What is artificial intelligence (AI)?
Cybercriminals are using phishing emails and malicious websites to spread Clickfix. The hospitality industry has been very attacked, with attackers that pass through Booking.com and sending false emails that refer to reviews or promotions of guests. When clicking on the links in these emails, he directs it to a clickfix trap. Health workers have also been attacked, with a malicious code integrated in the highly used physiotherapy site HEP2GO.
Once Clickfix is on its PC, it installs several types of malware, including password stolen such as XWORD, Lumma Stealer and Danabot, which extract their login credentials and financial information. Some versions offer remote access Trojans such as Venomrat and Asyncrat, giving the attackers total control over their system. Others implement Netsupport Rat, a remote access tool commonly misused for cyber espionage.
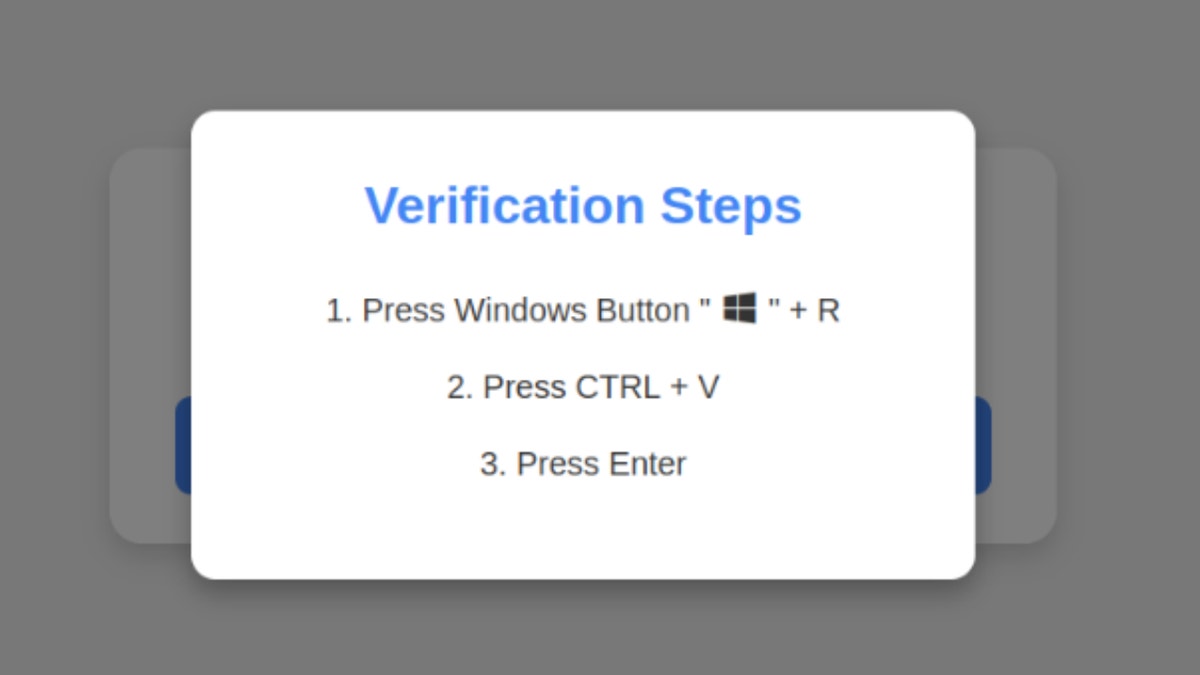
The execution of this Keypresses series asks Windows to download password theft malware. (Krebsosecury)
The hidden costs of free applications: your personal information
Previous click attacks
Security researchers believe that Clickfix has been pointing to people since March 2024. I reported on malware in June 2024 when Posed as false errors of Google Chrome, Word and OneDrive To deceive users to download a harmful code. As in the current campaign, the attackers led the victims to click on a button that copied a “fix” Powershell to the clipboard, then paste it and execute it in an execution dialog or a Powershell message.
In November 2024, attackers had expanded its goals to Google Meet users. The scam began with an email containing a link to a Google Meet session, often disguised as it was from the victim’s organization. This link leads to an invitation for a meeting, web seminar or online collaboration. By clicking on the link, he directed the victim to a false page of Google Meet, which showed a warning that stated that there was a problem with its PC, such as problems with its microphone, camera or headphones.
The attack was also seen in false Chrome error pages and Facebook login indications, extending malware on different platforms and increasing its reach.
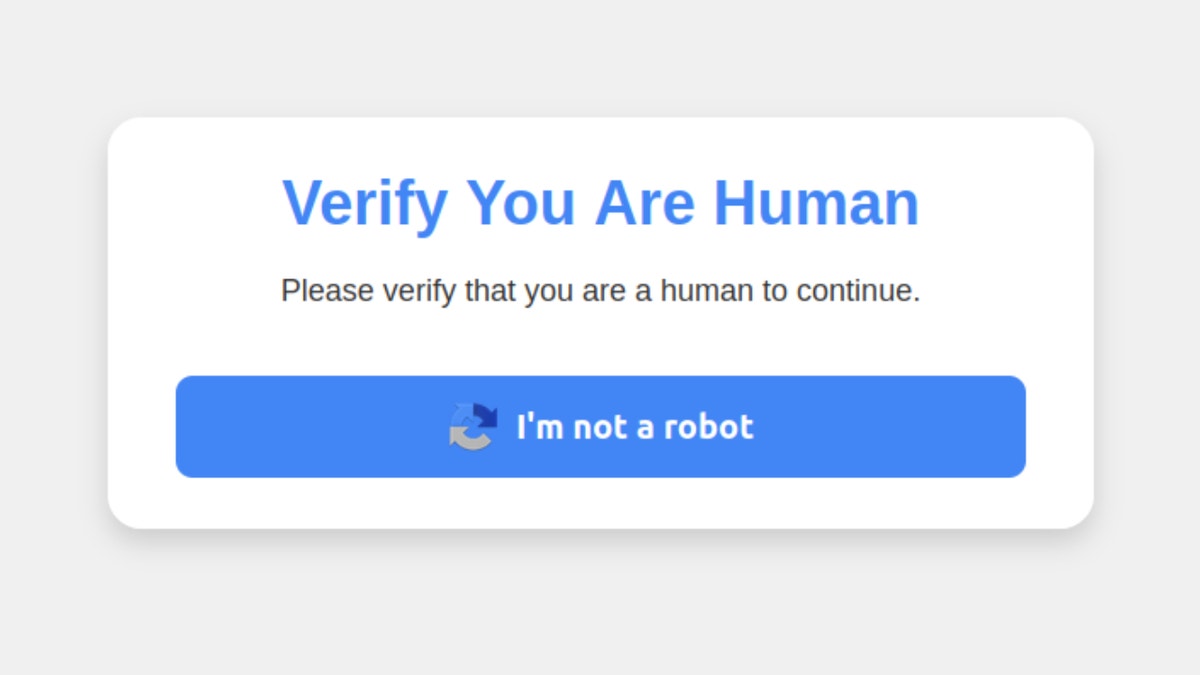
This malware attack aims to be a captcha destined to separate humans from the bots. (Krebsosecury)
Hackers who are to steal their identity
6 ways in which you can keep the malware clickfix
To protect themselves from the evolutionary threat of clickfix malware, which continues to address users through sophisticated social engineering tactics, consider implementing these six essential security measures.
1. Be skeptical of the captcha indications: Legitimate captcha tests never require Windows + R, copy commands or stick anything in Powershell. If a website tells you to do this, it is likely to be a scam. Close the page immediately and avoid interacting with it.
2. Do not click links from emails not verified and use strong antivirus software: Many Clickfix attacks begin with phishing emails that are passed through trusted services such as Booking.com or Google Meet. Always check the sender before clicking on the links. If an email seems urgent or unexpected, go directly to the company’s official website instead of clicking any link inside the email.
Get the News business on the fly by clicking here
The best way to safeguard the malicious links that install malware, which potentially access their private information, is to have strong antivirus software installed on all its devices. This protection can also alert it to the PHISHING Electronic Correos and Ransomware scams, maintaining their personal information and their safe digital assets. Get my elections for the best antivirus protection winners 2025 for your Windows, Mac, Android and iOS devices.
3. Enable two factors authentication: Allow two factors authentication whenever possible. This adds an additional security layer when requiring a second form of verification, such as a code sent to your phone, in addition to your password.
4. Keep updated devices: Regularly Update of your operating system, browser and safety software He assures that he has the last patches against known vulnerabilities. Cybercounts exploit obsolete systems, so allowing automatic updates is a simple but effective way to stay protected.
5. Monitor your accounts for suspicious activity and change your passwords: If you have interacted with a suspicious website, a Phishing email or a false login page, see your online accounts to obtain any unusual activity. Look for unexpected login attempts, unauthorized password remains or financial transactions that you do not recognize. If something seems off, change your passwords immediately and report the activity to the relevant service provider. In addition, consider using a password administrator to generate and store complex passwords. Get more details about me The best password administrators reviewed by experts of 2025 here.
6. Invest in the personal data elimination service: Consider using a service that monitors your personal information and alerts it to possible infractions or the unauthorized use of your data. These services can provide early warning signals of identity theft or other malicious activities resulting from clickfix or similar attacks. While no service promises to eliminate all its Internet data, having an elimination service is excellent if you want to constantly monitor and automate the process of eliminating your information from hundreds of sites continuously for a longer period of time. See my best selections to obtain data removal services here.
The mass security failure puts most popular browsers at risk in Mac
Kurt key takeway
Clickfix is a reminder that malware does not always trust complex feats. Often you just need to follow the incorrect instructions. The attackers are refining their methods, making scams such as fake captchas, emails of phishing and more convincing ever convincing emerging windows than ever. The best way to stay at the forefront is to question anything that seems a bit off. If a website asks you to run commands or stick something in Powershell, it is a red flag. If an email presses it to click on a link, check it first.
Click here to get the News application
Do you think technological companies are doing enough to stop malware as clickfix? Get us knowing in Cyberguy.com/contact.
To obtain more technological tips and safety alerts, subscribe to my free Cyberguy Report newsletter when you head Cyberguy.com/newsletter.
Ask Kurt or tell us what stories you would like us to cover.
Follow Kurt in his social channels:
- YouTube
Answers to the most informed Cyberguys questions:
- What is the best way to protect your MAC devices, Windows, iPhone and Android to be pirate?
- What is the best way to stay private, safe and anonymous while navigating the web?
- How can I get rid of robocalls with data elimination applications and services?
- How do I eliminate my private internet data?
New Kurt:
- Try the new Cyberguy games (crosswords, words searches, trivia and more!)
- Cyberguy exclusive coupons and offers
Copyright 2025 Cyberguy.com. All rights reserved.
Kurt “Cyberguy” Knutsson is a award -winning technological journalist who has a deep love for technology, equipment and devices that improve life with their contributions for News & News Business Startzing Mornings in “News & Friends”. Do you have a technological question? Get the free Kurt’s free newsletter, share your voice, an idea of the story or comment on Cyberguy.com.



