Implacable computer pirates leave the windows to aim at their Apple ID
If there is something that has been clarified during the past year, it is that Apple devices are not as safe as the company wants it to create.
We are four months in 2025 and there have already been more than 10 cases in which the attackers were specifically addressed to Apple users, and these are only the incidents we know.
I admit that no device is infallible, but there seems to be a growing trend in which bad actors prefer to address Apple users on other platforms. In fact, security researchers have recently identified a new Phishing campaign in which computer pirates, who previously focused on Windows, are now fixing their sights on Apple IDs.
Stay protected and informed! Get security alerts and expert technology advice: register at the ‘The Cyberguy Report’ of Kurt now

A person who works on a laptop from Apple (Kurt “Cyberguy” Knutsson)
What you need to know
Security researchers in Layerx laboratories They have discovered a new Phishing campaign that is specifically addressed to Mac users, marking a change of their previous approach in Windows. Initially, the attackers attracted Windows users with Microsoft false security alerts designed to steal login credentials. However, after Microsoft, Chrome and FireNews implemented new security features to block these attacks, computer pirates began to redirect their efforts towards Mac users.
The new attack closely reflects its predecessor but with key modifications. Phishing pages have redesigned to resemble Apple’s security warnings, making them seem legitimate for macOS users. The attack code has also been adjusted to specifically detect macOS and Safari users, ensuring that only Apple users see fraudulent pages.
In addition, despite changing their approach, the attackers continue to host these phishing pages in Microsoft Windows[.]Net domain Since this is a trusted Microsoft platform, it allows Phishing pages to evade security tools that evaluate the risk based on domain reputation.
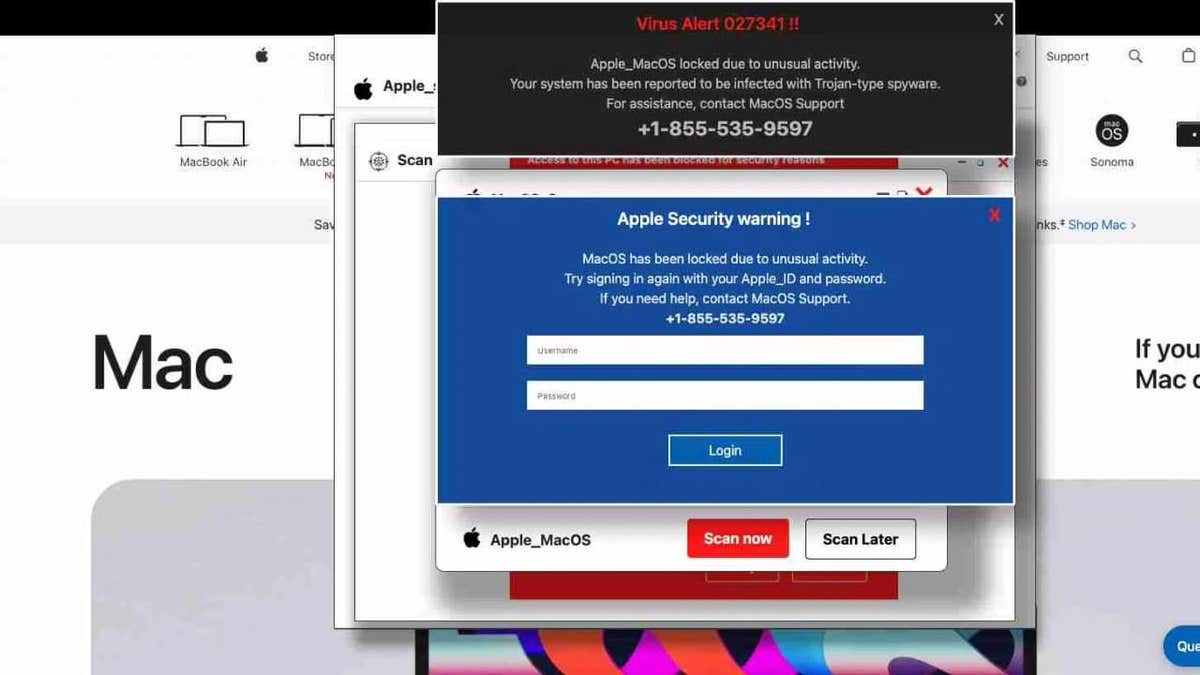
Committed websites that show false security warning (Layerx)
The FBI warns about a new scam of ‘dangerous’ smishing that goes to his phone
How victims attract in
The Phishing campaign exploits common but highly effective methods called typographic writings and malicious redirects. The victims often end in these phishing pages after making a simple mistake, such as hiding a URL while trying to visit a legitimate website.
Instead of arriving at the planned site, they land in a compromised domain parking lot. From there, they are redirected through multiple websites before reaching the Phishing page, which presents a false security warning of Apple. Believing that their identification of Apple is at risk, the victims are deceived to enter their credentials, without knowing it, giving them the attackers.
A remarkable case involved a person who used Safari who worked in a business secured by a safe web gateway. Despite the security measures of the organization, Phishing’s attempt managed to avoid the gateway protections.
What is artificial intelligence (AI)?
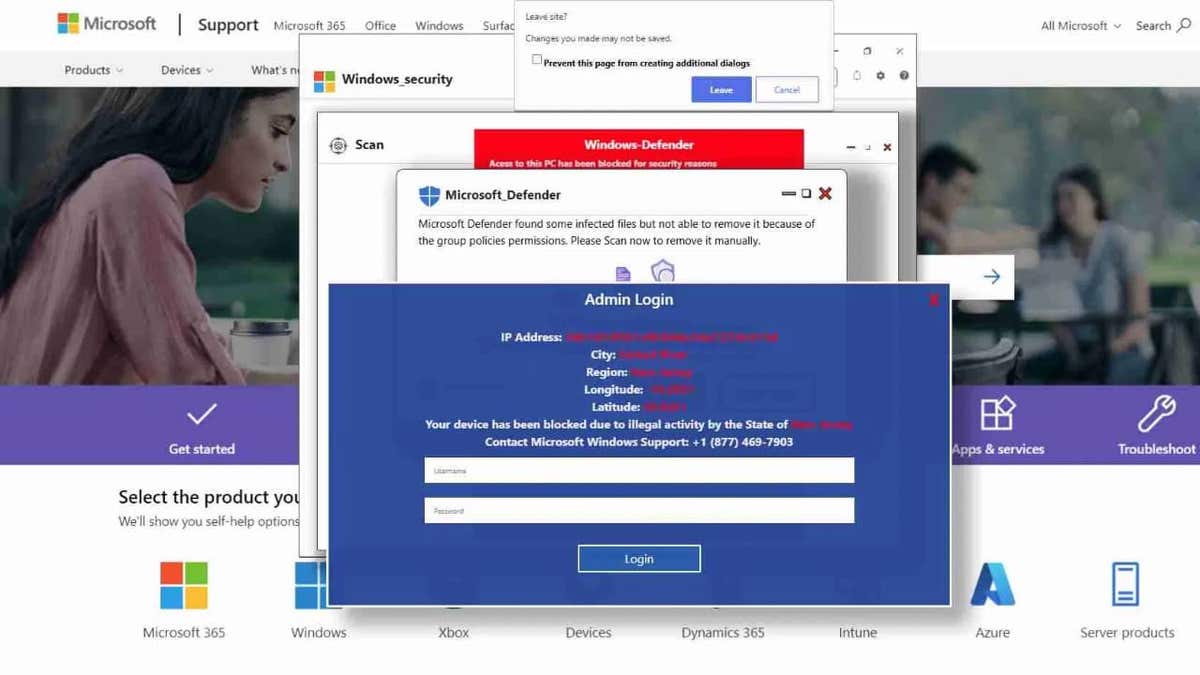
Committed websites that show false security warning (Layerx)
Apple’s Vulnerability exposes iPhones to attacks by stealthy computer pirates
7 ways to stay safe from attackers aimed at Apple users
Phishing campaigns are increasingly aimed at macOS users, but you are not helpless. There are four essential steps to protect yourself.
1. Use strong antivirus software: A reliable antivirus program is its first line of defense against phishing attempts and malicious websites. Although Apple’s incorporated security characteristics provide some protection, they are not infallible, especially against the sophisticated phishing attacks that imitate Apple’s legitimate warnings. A robust antivirus solution can detect and block malicious sites before even communicating them with them, preventing their credentials from accidentally entering on a fraudulent page. In addition, advanced safety software can identify suspicious redirects and alert it before being a victim of typographic writing. Get my elections for the best antivirus protection winners 2025 for your Windows, Mac, Android and iOS devices.
2. Keep your updated software: Regular Updates to macOS and their applications It is not just about new features. They are critical patches that fix security vulnerabilities. The attackers are rushed to exploit any weakness, so guarantee that their operating system and all the installed software are current minimizes the risk of a violation. Enable automatic updates whenever possible so that it is always protected by the latest security improvements.
3. Regularly monitor your Apple ID activity: Even with strong security measures, it is important to monitor your Apple ID account for any unauthorized access sign. Apple allows users to review the activity of their account, including devices registered in the account and recent changes. Regularly verify your Apple ID settings to ensure that only trust devices are connected and that no suspicious activity has occurred. If you notice something unusual, such as login attempts of unknown locations, immediately change your password and eliminate unauthorized devices. This proactive approach can help you detect possible early offenses and minimize damage.
Get the News business on the fly by clicking here
4. Enable two factors (2FA): Strong and unique passwords for each account are essential, but are even more effective when combined with two factors authentication. Even if the attackers manage to steal their credentials through a phishing attack, 2fa Add an additional barrier that makes unauthorized access significantly more difficult. Consider using a Password administrator to generate and store complex passwords. Get more details about me The best password administrators reviewed by experts of 2025 here.
5. Use a recovery key for improved security: Apple offers an optional feature called recovery key, which is a code of 28 characters that provides an additional security layer for its Apple ID. When enabling a recovery key, Apple disables its standard account recovery process, which means that you will need this key, together with access to a trusted device or phone number, to restore your password or recover access to your account. This makes it significantly more difficult for attackers to take control of their account.
To configure a recovery key, go to Configuration> [Your Name] > Locate and security> recovery key On your iPhone, iPad or Mac. Follow the indications to generate and confirm your recovery key. Be sure to write it and store it in a safe location, such as a safe or with a member of the trusted family. Keep in mind that losing both your recovery key and access to trust devices can permanently block it outside your account. However, if used in a responsible manner, this characteristic gives you greater control over the safety of your account.
6. Enable biometric authentication: Apple devices offer advanced Biometric authentication options such as Face and Tactal IDwhich provide an additional security layer. These characteristics make it significantly more difficult for attackers to access their device or confidential accounts, even if they manage to steal their credentials. Enable biometric authentication whenever possible, especially for applications and services that store personal or financial information. Since biometric data is unique to you, add a level of protection that passwords alone cannot provide.
7. Practice safe navigation: Many attacks are based on simple user errors, such as hiding a URL or clicking suspicious links. Always verify that you are visiting legitimate websites before entering any personal information. Be skeptical of unexpected security alerts, even if they mimic Apple design. Learning to identify the subtle signs of phishing, such as unusual URL structures or generic greetings, can help you avoid falling into these scams.
How to protect your iPhone and IPAD from malware
Kurt’s Key Takeways
Apple has long sold the idea that its ecosystem is inherently safer than alternatives, but that statement is beginning to wear. The reality is that the attackers no longer ignore Mac users, they are actively attacking them, and Apple’s response has been everything but proactive. While Microsoft, Google and others launch new security measures to counteract evolving threats, Apple is still slow to adapt, depending on obsolete assumptions about the safety of its platform.
Click here to get the News application
Do you think Apple should be more transparent about security vulnerabilities that affect its users? Get us knowing in Cyberguy.com/contact.
To obtain more technological tips and safety alerts, subscribe to my free Cyberguy Report newsletter when you head Cyberguy.com/newsletter.
Ask Kurt or tell us what stories you would like us to cover.
Follow Kurt in his social channels:
- YouTube
Answers to the most informed Cyberguys questions:
- What is the best way to protect your MAC devices, Windows, iPhone and Android to be pirate?
- What is the best way to stay private, safe and anonymous while navigating the web?
- How can I get rid of robocalls with data elimination applications and services?
- How do I eliminate my private internet data?
New Kurt:
- Try the new Cyberguy games (crosswords, words searches, trivia and more!)
- Cyberguy exclusive coupons and offers
Copyright 2025 Cyberguy.com. All rights reserved.
Kurt “Cyberguy” Knutsson is a award -winning technological journalist who has a deep love for technology, equipment and devices that improve life with their contributions for News & News Business Startzing Mornings in “News & Friends”. Do you have a technological question? Get the free Kurt’s free newsletter, share your voice, an idea of the story or comment on Cyberguy.com.



